Nginx secure HTTPS settings
nginx, ssl | July 16, 2015
Edit: updated February 15, 2016.
Recently, OpenSSL has been under fire for being not secure and people have become increasingly aware of the the fact that they need to provide their webservers with the right settings for HTTPS certificates. The defaults are often not secure. These are the configuration settings that I use in Nginx vhosts:
ssl on; ssl_certificate /etc/ssl/certs/yourdomain.crt; ssl_certificate_key /etc/ssl/private/yourdomain.key; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA; ssl_prefer_server_ciphers on; ssl_session_timeout 5m; ssl_session_cache shared:SSL:5m;
- ssl_protocols: no SSL protocols are secure, you must use TLS only
- ssl_ciphers: unless you must support IE6, this will be just fine. My ciphers are based on Mozilla's recommended configurations, then tweaked with CipherScan and checked with Qualys SSL Labs server test and testssl to support all browsers.
- ssl_prefer_server_ciphers: prefer the server ciphers over client ciphers
- ssl_session_timeout: allows session reuse
- ssl_session_cache: by default sessions are not cached
You can check your own settings at Qualys SSL Labs server test. With the above settings, you will get an A rating. Eg:
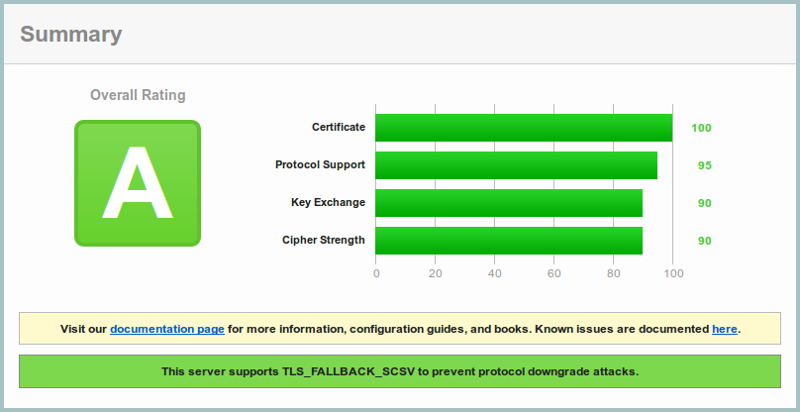
To get an A+ rating, enable the Strict-Transport-Security (HSTS) header. This will make sure your browser will never visit the site over HTTP during the periode of the max-age of the header.
add_header Strict-Transport-Security "max-age=31536000";
There are a lot more headers to consider. For example: Content-Security-Policy, Public-Key-Pins, X-Frame-Options, X-XSS-Protection, X-Content-Type-Options. See securityheaders.io to check the headers of your own site. The site also has information about what these headers protect against.
It is also recommended to enable OCSP stapling.
ssl_stapling on; ssl_stapling_verify on; ssl_trusted_certificate /etc/ssl/certs/fullchain.crt;